Oh boy ! I have 500 Linux VM to protect !

Chill out and kick back.
Grab your favorite geek mug, fill it with your top-notch black coffee, and let the code command !
The plan :
- Use Ansible as the automation tool / Acronis as protection tool
- Create inventory files for the VMs
- Create playbook (YAML config file) to manage Acronis agent installation
- Manage agent registration to the cloud
- See the slave to work and enjoy your coffee
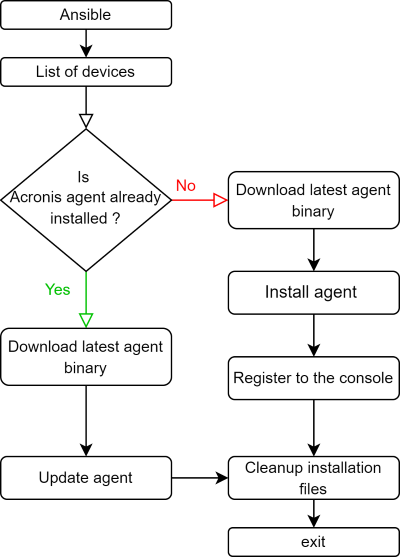
Process flow diagram:
So, first thing first, let's install Ansible on the device who will act as a master control for the deployment on the 500 Vms.
(I will use a Debian12 vm)
As usual let's start by latest updates
sudo apt update && sudo apt upgrade -ythen install dependencies
sudo apt install software-properties-commonAdd Ansible’s official repository
sudo apt update
sudo apt install -y gnupg2
echo 'deb http://ppa.launchpad.net/ansible/ansible/ubuntu focal main' | sudo tee /etc/apt/sources.list.d/ansible.list
Add Ansible’s repository key
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 93C4A3FD7BB9C367
Install Ansible
sudo apt update
sudo apt install ansible
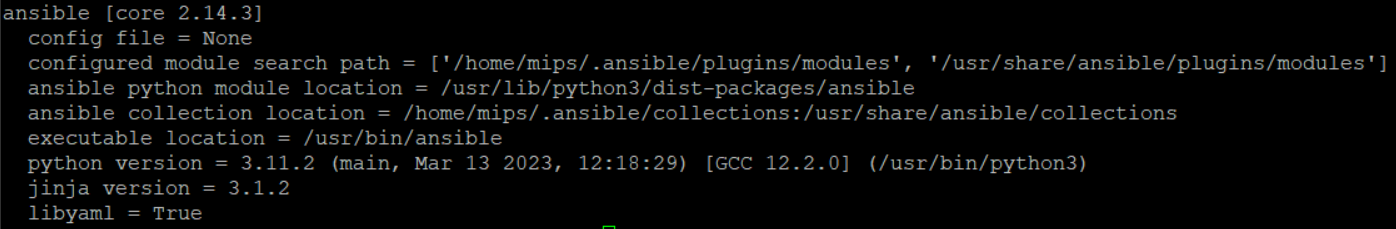
check if Ansible is installed
ansible --version
you should see something like that:
Now, create folder for the hosts inventory file
sudo mkdir -p /home/ansible/hosts
cd /home/ansible/hostscreate hosts inventory file
sudo nano hostsinventory a new group of devices called 'deployacronis'
[deployacronis]
10.0.4.64
10.0.4.36create a folder to stores Ansible playbooks
cd ..
sudo mkdir playbook
cd playbookCreate playbook file to deploy Acronis agent
sudo nano deploy-acronis.ymlBelow the yaml file.
"https://to_the_acronis_binary" -> should be the http path where to find acronis binary file (acronis_agent_installer.bin)
<your-cloud-url> -> acronis url for your tenant (like https://cloud.acronis.com)
<token> -> the token generated from your tenant
- hosts: "deployacronis"
become: yes
tasks:
- name: Check if Acronis Agent is installed
ansible.builtin.shell: systemctl is-active --quiet acronis* # This command checks if any Acronis service is active
register: acronis_service_check
ignore_errors: yes
- name: Download Acronis Agent
ansible.builtin.get_url:
url: https://to_the_acronis_binary
dest: /tmp/acronis_agent_installer.bin
mode: '0755' # Sets the installer as executable
- name: Install Acronis Agent
ansible.builtin.shell: >
/tmp/acronis_agent_installer.bin -i BackupAndRecoveryAgent -a --rain=<your-cloud-url> --token=<your cloud token>
when: acronis_service_check.rc != 0 # Install if Acronis Agent is not active
- name: Update Acronis Agent
ansible.builtin.shell: >
/tmp/acronis_agent_installer.bin -a --token=<your cloud token>
when: acronis_service_check.rc == 0 # Update if Acronis Agent is active
- name: Remove Acronis Agent installer
ansible.builtin.file:
path: /tmp/acronis_agent_installer.bin # Specify the path to the installer that needs to be removed
state: absent # Ensures the file is removedOK boys, all done now !
let execute the script.
run the following command at Ansible root folder :
sudo ansible-playbook playbooks/deploy-acronis.yml --key-file "/home/greg/ansible/id_rsa" --user=greg --ask-become-pass --ssh-common-args='-o StrictHostKeyChecking=no'some explanation of the command :
- 'ansible-playbook' : command to run playbook follow by the playbook path
- --key-file : path to you key needed by ssh remote access to the hosts
- --user : use a specific user
- --ask-become-pass : to become when escalation is need like 'sudo'
- --ssh-common-args= : to not use only ssh keys when connection to hosts
Now it's time to kick back, my friends.
Grab your coffee, relax, and let your new digital minion handle the heavy lifting!

Result should be the following
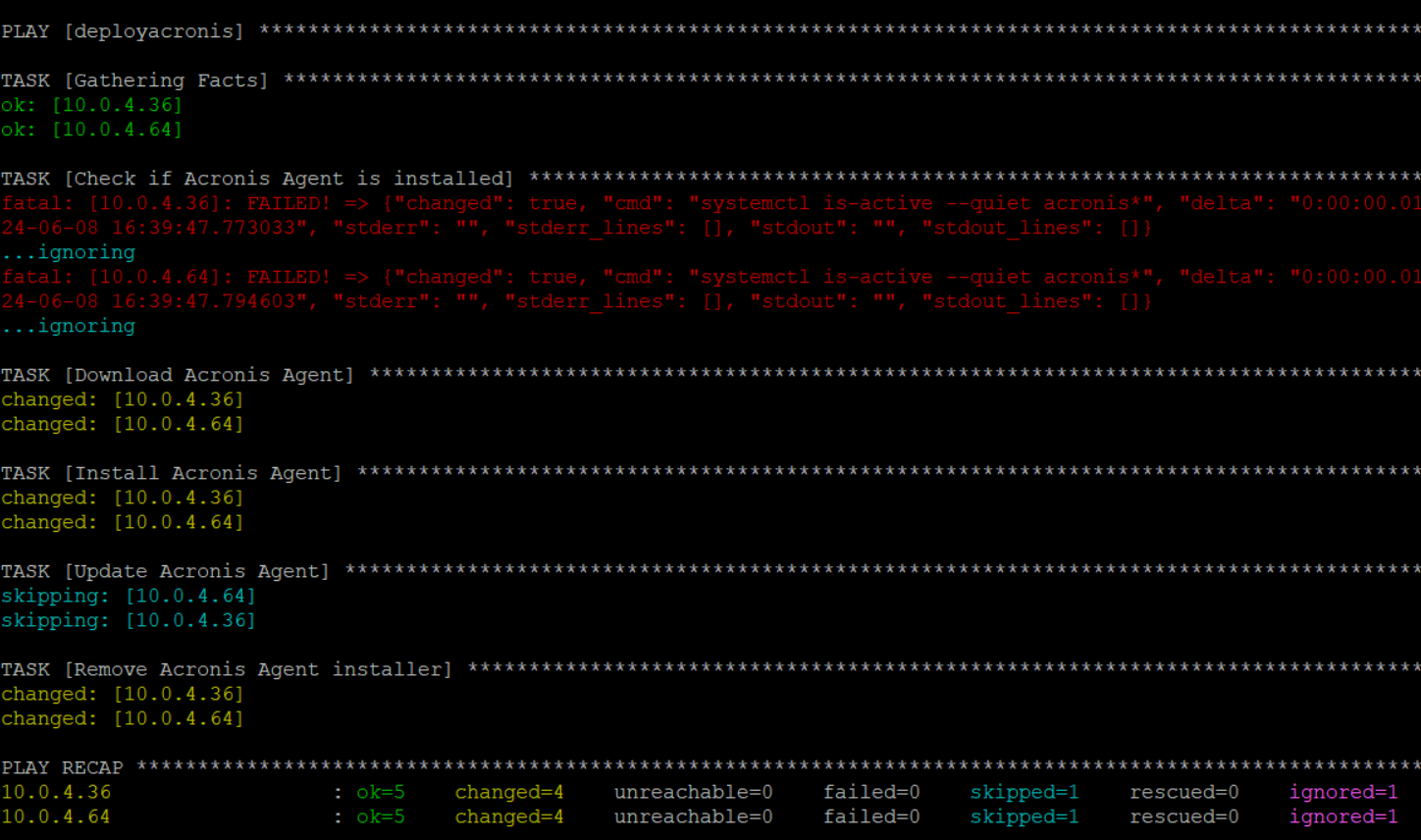
fatal error is normal. It's just because the Acronis agent wasn’t installed on these VMs—so no update was needed anyway.